Hybrid cloud networking
A traditional multisite LAN network may need to connect several branch offices to a headquarters. In the same way, a hybrid cloud network involves using appropriate technologies to continuously interconnect on‑premises users, and on‑premises applications and data with cloud‑hosted applications and data.
In our scenario, Tailwind Traders must be able to securely connect its on‑premises sites to resources running in Azure. For Tailwind Traders staff, there should be no real difference between accessing a workload that runs in a Tailwind Traders on‑premises datacenter and one that runs in Azure.
In this unit, you will learn about the networking technologies that enable on‑premises and cloud resources to be networked into a single hybrid cloud.
What is an Azure VPN?
An Azure VPN gateway allows you to connect your on‑premises network to Azure by using a secure VPN tunnel over the public Internet. Azure VPN connections are similar to traditional connections that may exist between a branch office and a headquarters location. Each virtual network can have only one VPN gateway, but each VPN gateway supports multiple connections.
The following image shows a connection between a perimeter gateway device on an on‑premises network and a VPN gateway on an Azure virtual network. It reflects the connection between an Azure Stack device and a VPN gateway.
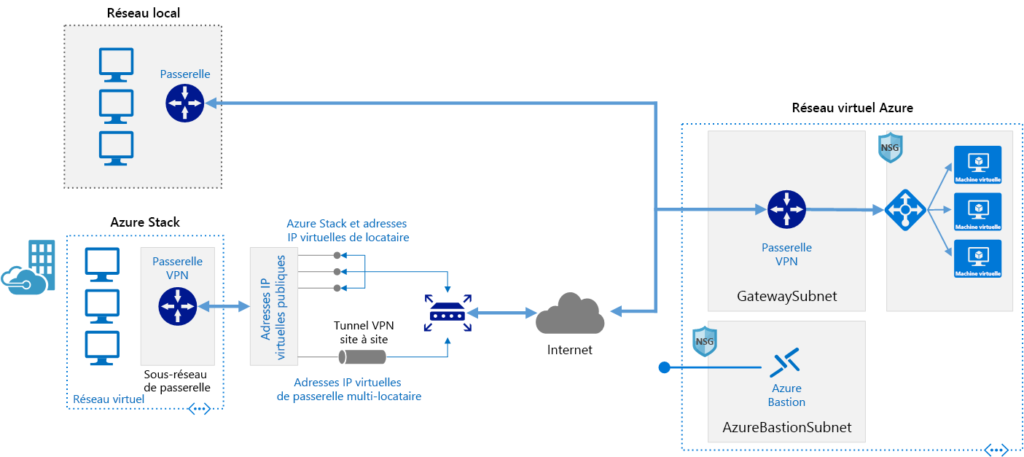
In the Tailwind Traders example, the company can use Azure VPN gateways to allow connections from smaller sites that do not need the type of dedicated link provided by an Azure ExpressRoute connection. The main disadvantage of Azure VPN gateways is that they rely on your Internet Service Provider’s (ISP) internet connection. If your ISP goes down, VPN connections cannot be established. Likewise, if your ISP experiences significant congestion, the speed of the VPN connection between an on‑premises site and Azure may degrade.
Organizations that use VPN connections between branch locations already face challenges related to dedicated VPN connections.
What is Azure ExpressRoute?
Microsoft Azure ExpressRoute enables an organization to benefit from a private, dedicated broadband connection between its on‑premises network and Azure. This connection does not pass over the public Internet. Functionally, it is a dedicated fiber‑optic line that directly connects an on‑premises site to the nearest Azure datacenter.
Unlike a VPN gateway, the ExpressRoute provider manages the equipment that provides this connection. Since the ExpressRoute provider manages all the equipment, it can provide a Service‑Level Agreement (SLA) based on reliability and bandwidth, which is not available for users of Azure VPN gateway connections.
The following image shows the ExpressRoute connection between the on‑premises environment and the workloads running in Azure. The ExpressRoute provider manages the ExpressRoute circuit and the on‑premises edge routers.
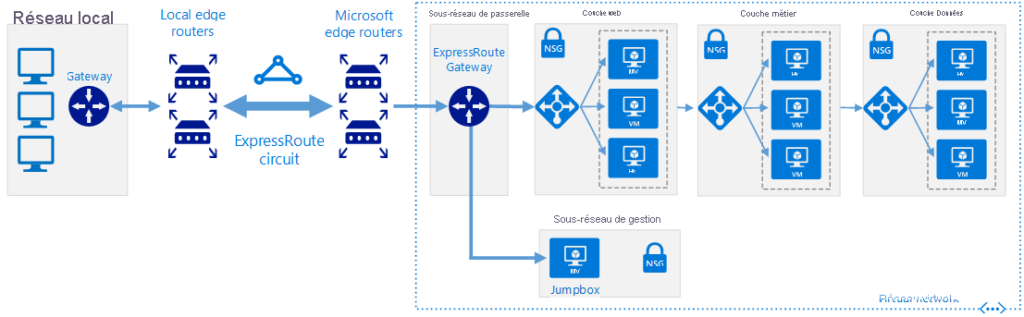
In addition to providing a dedicated bandwidth connection between the on‑premises environment and Azure, ExpressRoute allows an organization to ensure that sensitive traffic does not pass over the public Internet. This type of connection is important in jurisdictions where governance requirements prohibit the transmission of certain types of information over the Internet.
In the case study example, Tailwind Traders can set up an ExpressRoute connection from larger offices such as Melbourne, Sydney, and Auckland, where more people are present. The company may also need to use ExpressRoute if certain types of managed data cannot be transferred over the Internet for compliance reasons.
What is Hybrid DNS?
When you implement a hybrid cloud, it is necessary to ensure that on‑premises workloads can resolve the addresses of cloud workloads, and that cloud workloads can resolve the addresses of on‑premises workloads. Domain Name System (DNS) deployments in a hybrid cloud typically require DNS servers on‑premises and in Azure. In addition, DNS zone transfers must be configured between the on‑premises environment and the cloud. An alternative is to configure DNS forwarders if the on‑premises DNS zone is separate from the DNS zone associated with workloads running in Azure.
The following image shows on‑premises DNS servers replicating DNS information to DNS servers running in Azure. In this scenario, a virtual machine is deployed as a DNS server in Azure. In the image, the on‑premises DNS connects a hub subscription with DNS servers in virtual machines. Other Azure subscriptions connect to the hub subscription.
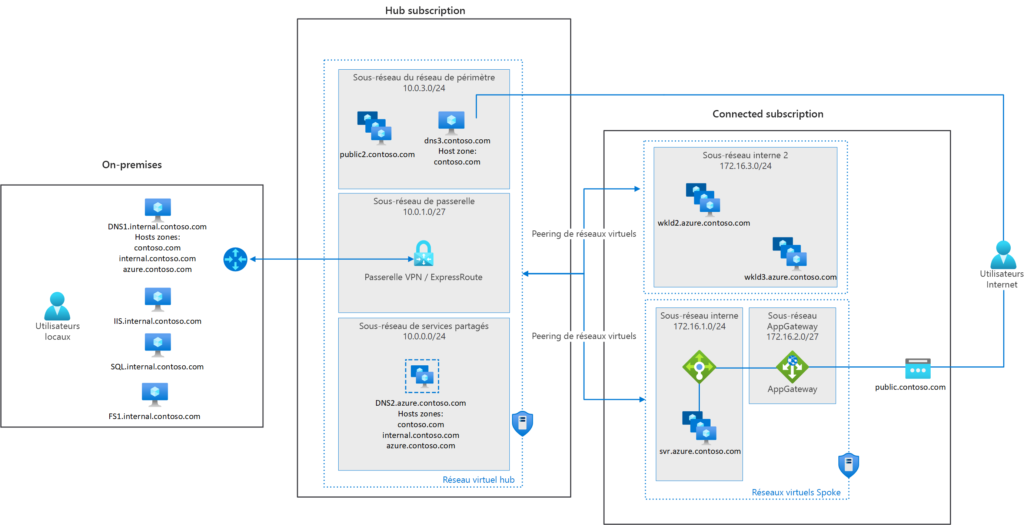
Alternatively, Azure DNS Private Resolver is a service that allows you to query Azure private DNS zones from an on‑premises environment, and vice versa, without deploying VM‑based DNS servers. The private resolution service is fully managed and has built‑in high‑availability features.
Tailwind Traders can use Azure DNS Private Resolver to ensure that all its workloads running in Azure can resolve the DNS names of hosts on the Tailwind Traders internal network. It also ensures that all hosts on the Tailwind Traders internal network can resolve the DNS names of workloads running in the cloud.
Introduction to Azure Virtual WAN
Azure Virtual WAN enables an organization to use the Azure network in a hub‑and‑spoke architecture. The Azure network functions as a hub for transitive connectivity between endpoints that function as spokes.
Traditionally, you may have a network topology where each branch has a VPN connection to the headquarters site. If traffic flows from one branch to another, it goes through the hub site to reach it. If the headquarters and branch sites are all connected to Azure, either through a VPN or ExpressRoute, these connections can form the spokes. Azure Virtual WAN can function as the routing hub for traffic between on‑premises sites.
The following image shows an Azure Virtual WAN topology.
